🔐 OIDC Authentication
SSO via OpenID Connect. Users log in with their existing identity provider.
Setup
Go to Settings → Authentication → Add Provider.
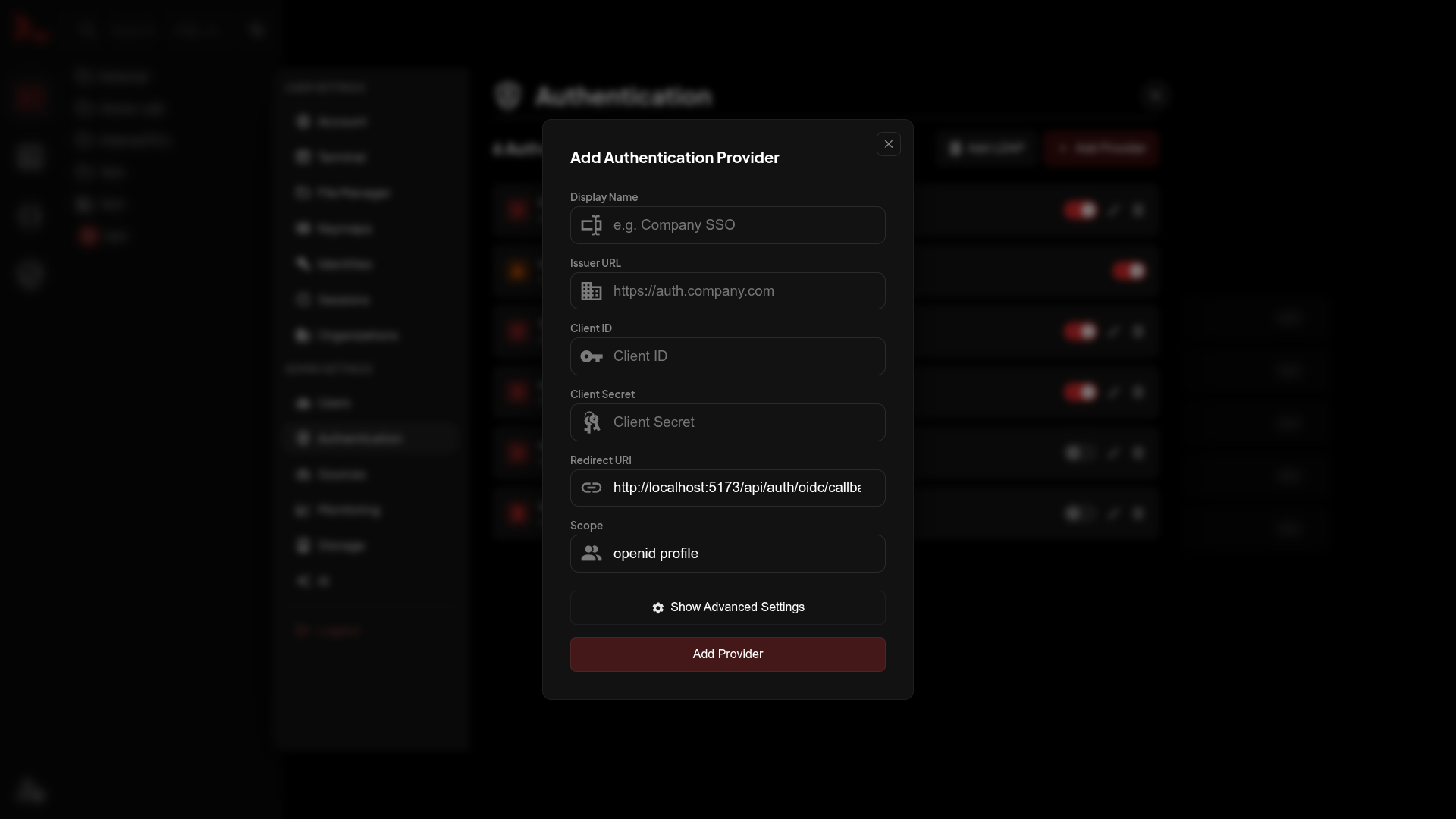
| Field | Description |
|---|---|
| Display Name | Shown on login button |
| Issuer URL | IdP's discovery URL |
| Client ID | From your IdP |
| Client Secret | From your IdP |
| Redirect URI | Copy this to your IdP |
| Scope | Usually openid profile |
Provider Setup
Microsoft Entra ID (Azure AD)
- Azure Portal → Microsoft Entra ID → App registrations → New registration
- Add redirect URI:
https://nexterm.yourdomain.com/api/auth/oidc/callback - Copy Application (client) ID → Client ID
- Certificates & secrets → New client secret → copy value → Client Secret
- Issuer URL:
https://login.microsoftonline.com/{tenant-id}/v2.0
Google
- Google Cloud Console → APIs & Services → Credentials
- Create Credentials → OAuth client ID → Web application
- Add redirect URI:
https://nexterm.yourdomain.com/api/auth/oidc/callback - Issuer URL:
https://accounts.google.com
WARNING
Google requires app verification for production. Add test users in OAuth consent screen during dev.
Keycloak
- Clients → Create client
- Enable Client authentication
- Add redirect URI, copy Client Secret from Credentials tab
- Issuer URL:
https://keycloak.yourdomain.com/realms/{realm-name}
Authentik
- Applications → Providers → Create → OAuth2/OpenID Provider
- Set redirect URI, copy Client ID/Secret
- Issuer URL:
https://authentik.yourdomain.com/application/o/{application-slug}/
TIP
The trailing slash matters. Check /.well-known/openid-configuration to see the exact issuer value.
Authelia
yaml
identity_providers:
oidc:
clients:
- client_id: nexterm
client_secret: '$pbkdf2-sha512$your-hashed-secret'
redirect_uris:
- https://nexterm.yourdomain.com/api/auth/oidc/callback
scopes: [ openid, profile, email ]Issuer URL: https://auth.yourdomain.com
Attribute Mapping
Defaults in Advanced Settings:
| Field | Claim |
|---|---|
| Username | preferred_username |
| First Name | given_name |
| Last Name | family_name |
Troubleshooting
Redirect URI mismatch - Must match exactly. Check trailing slashes, http vs https.
User attributes wrong - Check claim names in your IdP's token and adjust mapping.